When Security Is Not A Factor: Secton
Introduction
We’re not seasoned penetration testers, nor do we specialize in software security. We just stumbled upon Secton, an obscure AI platform, by jumping through a variety of their developers' open-source projects by chance, and decided to do a little digging for fun. The results were … very interesting, to say the least. Even with minimal experience, we uncovered a variety of basic security pitfalls.
What is Secton?
First off, from what I understand, Secton is a platform similar to OpenAI or Anthropic, looking to provide AI models as a service.
They appear to market directly to developers and provide "Modular APIs", "Human-first UX", and "Security baked in" per their website, along with apparently providing a cost-friendly AI integration.
With your context about the claims made by this company set, it's time to dive into our findings brought forth in only four hours.
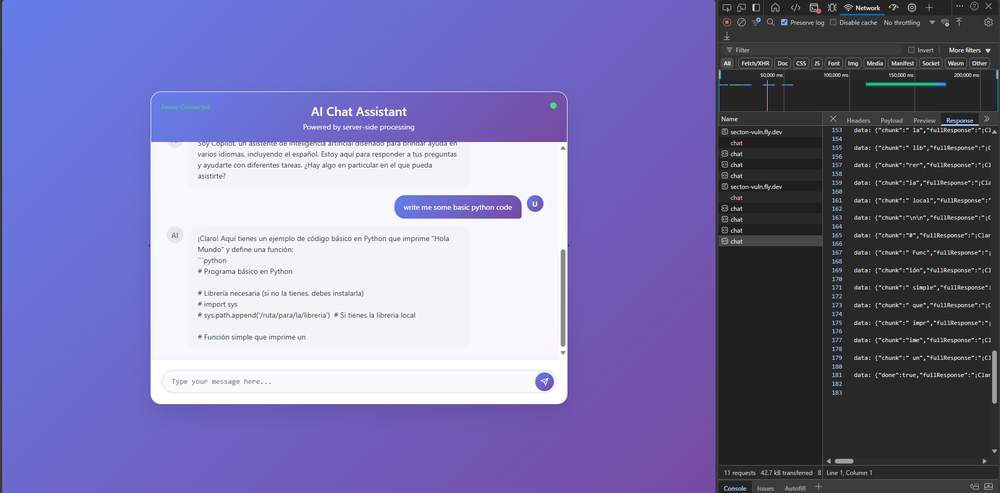
Bypassing Client-Side Rate Limits In Secton Copilot
Here is the simplest exploit ever.
1. Right-click the textarea in browser, choose "Inspect Element".
2. Remove "disabled" attribute.
3. Keep sending requests indefinitely.
No extra knowledge needed, no account creation needed, no diving into DNS records needed. Just a simple right click, and the removal of the disabled attribute.
Now, it's not like they didn't have limits, they had an endpoint on https://copilot.secton.org/api/chat/guest-limits, which did correctly decrease the remaining count per IP ...
{
"ip": "HEHE-NO-IP-FOR-YOU",
"count": 10,
"limit": 10,
"remaining": 0,
"resetAt": "2025-06-23T17:17:24.201Z"
}However, the API you called at https://copilot.secton.org/api/chat doesn't respect the guest rate-limiting, and you can just... bypass it.
For a quick example of using this endpoint, see below!
const response = await fetch("https://copilot.secton.org/api/chat", {
body: '{"prompt": "hi"}',
cache: "default",
credentials: "include",
headers: {
Accept: "*/*",
"Accept-Language": "en-GB,en;q=0.9",
"Cache-Control": "no-cache",
"Content-Type": "application/json",
Pragma: "no-cache",
Priority: "u=3, i",
"User-Agent":
"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/18.5 Safari/605.1.15",
},
method: "POST",
mode: "cors",
redirect: "follow",
referrerPolicy: "no-referrer",
}).then((r) => r.text());data: {"response":"Hello","p":"abcdefghijklmnopqrstuvw"}
data: {"response":"!","p":"abcdefghijklmnopqrstuvw"}
data: {"response":" How","p":"abcdefgh"}
data: {"response":" can","p":"abcdefghijklmnopqrstuvwxyz0123456789abcdefgh"}
data: {"response":" I","p":"abcdefghijklmnopqrstuv"}
data: {"response":" assist","p":"abcdefghij"}
data: {"response":" you","p":"abcdefghijklmnopqrstuvwxyz012345"}
data: {"response":" today","p":"abcdefghijklmnopqrstuvwxyz0"}
data: {"response":"?","p":"abcdefghijklmnopqrstuvwxyz0123456789abcdefghij"}
data: {"response":""}
data: {"response":"","usage":{"prompt_tokens":755,"completion_tokens":10,"total_tokens":765}}
data: [DONE]Gaining Full Playground Access
Now, given the past failure to correctly authenticate endpoints, can you guess what's up next?
If you thought it was another unauthenticated endpoint, you'd be wrong! Unlike the other one, this did require exploring a tiny bit and creating an account. Once you were signed up, they had a playground you could use to test out the models, which I assumed used my authentication token or some unique one for this. I was wrong, I found that they just had a completely public and free-to-use bearer token called playground. Okay, well, it must have some rate-limiting, etc, nope. Just like the copilot API, it gives you access to not 1 but both of their models, for free, no credits deducted, and pretty much no rate-limiting (assuming you don't count the server itself throwing 500s when you send a batch of 2,000 requests at once).
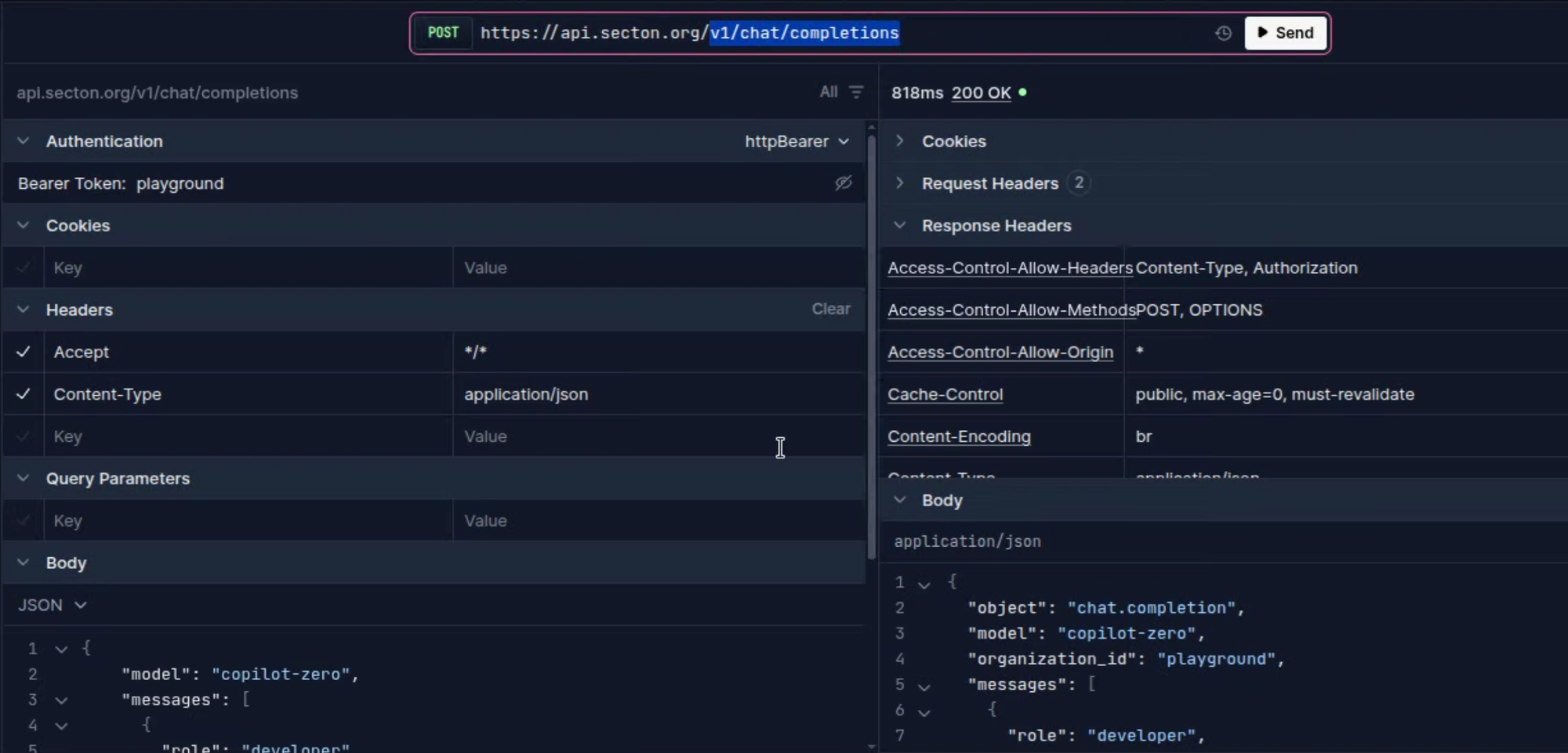
Even more Free AI
Welp, you know the pattern, time to find another unauthenticated endpoint that gives me more free AI!
This time we do need to do a little digging, with some quick searching via dnsdumpster.com, we can find two sub-domains, ai-compute and speech-compute. Wanna guess whether they have authentication?
Let's give speech-compute.secton.org a try first.
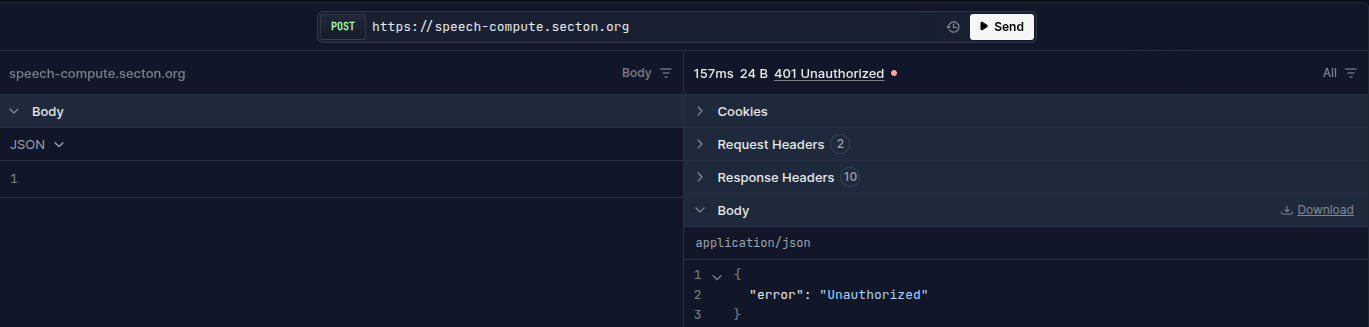
Well, would you look at that! They at least have some common sense to block that route, now what if we try ai-compute.secton.org next? Well, well, well, more free AI for me! (I forgot to take a screenshot, shhh)
In total, that is 3 different methods across 3 different subdomains where I can go and get unlimited, unprotected, and near non-existent rate-limiting for a noticeably slower, lower-accuracy model.
Mitigations
As was noted earlier, we did disclose these problems with the developers, as I've been informed, all issues/bugs/exploits/vulnerabilities have been patched and pushed to production.
Clearing the Air
Despite having little formal experience in penetration testing, we discovered significant security lapses at Secton in just a few hours of casual investigation.
I truly don't know if their code was AI-generated or if their developers are juniors who are still learning, though I don't believe I have the true right to judge that. However, I do hope that at least they took this with a stride and learn from it.
Credits
- noClaps, for locating the initial bug in Secton Copilot, you may find him at zerolimits.dev
- RollViral, for assisting in testing and locating bugs
"Disclaimer: This article is provided for educational purposes and responsible disclosure. We do not endorse exploiting live systems without permissions. Furthermore during tested we did our best to keep our usage with-in the default number of tokens provided for new accounts created on platform.secton.org"